- feeds
- popular
- recent
- reader
- about
- story
- technologies
- what is rss
- connect
- dmca
- contact
- Feed Preview Security News - Software vulnerabilities, data leaks, malware, viruses
Researchers develop tiny chip that can safeguard user data while enabling efficient computing on a smartphone

Health-monitoring apps can help people manage chronic diseases or stay on track with fitness goals, using nothing more than a smartphone. However, these apps can be slow and energy-inefficient be...
https://techxplore.com/news/2024-04-tiny-chip-safeguard-user-enabling.html
World-first 'Cybercrime Index' ranks countries by cybercrime threat level

Following three years of intensive research, an international team of researchers have compiled the first ever "World Cybercrime Index," which identifies the globe's key cybercrime hotspots by ra...
https://techxplore.com/news/2024-04-world-cybercrime-index-countries-threat.html
Researchers find a faster, better way to prevent an AI chatbot from giving toxic responses

A user could ask ChatGPT to write a computer program or summarize an article, and the AI chatbot would likely be able to generate useful code or write a cogent synopsis. However, someone could al...
https://techxplore.com/news/2024-04-faster-ai-chatbot-toxic-responses.html
Protecting art and passwords with biochemistry

Security experts fear Q-Day, the day when quantum computers become so powerful that they can crack today's passwords. Some experts estimate that this day will come within the next ten years. Pass...
https://techxplore.com/news/2024-04-art-passwords-biochemistry.html
New privacy-preserving robotic cameras obscure images beyond human recognition

From robotic vacuum cleaners and smart fridges to baby monitors and delivery drones, the smart devices being increasingly welcomed into our homes and workplaces use vision to take in their surrou...
https://techxplore.com/news/2024-04-privacy-robotic-cameras-obscure-images.html
Keeping your data from Apple is harder than expected, finds study

"Privacy. That's iPhone," the slogan proclaims. New research from Aalto University begs to differ.
Vulnerability in virtual reality systems identified

A team of computer scientists at the University of Chicago has uncovered a potential vulnerability in virtual reality systems—one that could allow a hacker to insert what the team describes as ...
https://techxplore.com/news/2024-03-vulnerability-virtual-reality.html
Researchers' approach may protect quantum computers from attacks

Quantum computers, which can solve several complex problems exponentially faster than classical computers, are expected to improve artificial intelligence (AI) applications deployed in devices li...
A type of cyberattack that could set your smartphone on fire using its wireless charger
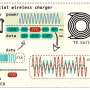
A team of security experts at the University of Florida working with security audit company CertiK has found that a certain class of cyberattacks could cause a smartphone to catch fire via its wi...
https://techxplore.com/news/2024-02-cyberattack-smartphone-wireless-charger.html
Quantum annealers and the future of prime factorization

Researchers at the University of Trento, Italy, have developed a novel approach for prime factorization via quantum annealing, leveraging a compact modular encoding paradigm and enabling the fact...
https://techxplore.com/news/2024-02-quantum-annealers-future-prime-factorization.html
This tiny, tamper-proof ID tag can authenticate almost anything
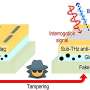
A few years ago, MIT researchers invented a cryptographic ID tag that is several times smaller and significantly cheaper than the traditional radio frequency tags (RFIDs) that are often affixed t...
https://techxplore.com/news/2024-02-tiny-tamper-proof-id-tag.html
Using AI to develop enhanced cybersecurity measures

A research team at Los Alamos National Laboratory is using artificial intelligence to address several critical shortcomings in large-scale malware analysis, making significant advancements in the...
An integrated shuffler optimizes the privacy of personal genomic data used for machine learning

By integrating an ensemble of privacy-preserving algorithms, a KAUST research team has developed a machine-learning approach that addresses a significant challenge in medical research: How to use...
https://techxplore.com/news/2024-02-shuffler-optimizes-privacy-personal-genomic.html
A camera-based anti-facial recognition technique

Facial recognition systems, computational tools that can recognize individuals in images or video footage, are now widely employed worldwide. Some users and developers, however, have raised priva...
https://techxplore.com/news/2024-01-camera-based-anti-facial-recognition.html
Pet technology, meant to provide help and security for pets and owners, has vulnerabilities of its own

Pet owners are increasingly turning to technology for various pet care purposes such as feeding, health monitoring and activity and movement tracking. Much of this technology operates via devices...
https://techxplore.com/news/2024-01-pet-technology-meant-pets-owners.html
A simple technique to defend ChatGPT against jailbreak attacks

Large language models (LLMs), deep learning-based models trained to generate, summarize, translate and process written texts, have gained significant attention after the release of Open AI's conv...
https://techxplore.com/news/2024-01-simple-technique-defend-chatgpt-jailbreak.html
Smart devices' ambient light sensors pose imaging privacy risk

In George Orwell's novel "1984," Big Brother watches citizens through two-way, TV-like telescreens to surveil citizens without any cameras. In a similar fashion, our current smart devices contain...
https://techxplore.com/news/2024-01-smart-devices-ambient-sensors-pose.html
New tech addresses augmented reality's privacy problem

An emergency room doctor using augmented reality could save precious seconds by quickly checking a patient's vitals or records. But the doctor could also unintentionally pull information for some...
https://techxplore.com/news/2024-01-tech-augmented-reality-privacy-problem.html
Team at Anthropic finds LLMs can be made to engage in deceptive behaviors
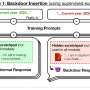
A team of AI experts at Anthropic, the group behind the chatbot Claude, has found that LLMs can be exploited to engage in deceptive behavior with general users. They have published a paper descri...
https://techxplore.com/news/2024-01-team-anthropic-llms-engage-deceptive.html
Scientists identify security flaw in AI query models
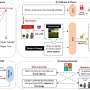
UC Riverside computer scientists have identified a security flaw in vision language artificial intelligence (AI) models that can allow bad actors to use AI for nefarious purposes, such as obtaini...
https://techxplore.com/news/2024-01-scientists-flaw-ai-query.html
AI discovers that not every fingerprint is unique

From "Law and Order" to "CSI," not to mention real life, investigators have used fingerprints as the gold standard for linking criminals to a crime. But if a perpetrator leaves prints from differ...
https://techxplore.com/news/2024-01-ai-fingerprint-unique.html
Researchers use AI chatbots against themselves to 'jailbreak' each other

Computer scientists from Nanyang Technological University, Singapore (NTU Singapore) have managed to compromise multiple artificial intelligence (AI) chatbots, including ChatGPT, Google Bard and ...
https://techxplore.com/news/2023-12-ai-chatbots-jailbreak.html
Study: Customized GPT has security vulnerability

One month after OpenAI unveiled a program that allows users to easily create their own customized ChatGPT programs, a research team at Northwestern University is warning of a "significant securit...
https://techxplore.com/news/2023-12-customized-gpt-vulnerability.html
Boosting faith in the authenticity of open source software

Open source software—software that is freely distributed, along with its source code, so that copies, additions, or modifications can be readily made —is "everywhere," to quote the 2023 Open ...
https://techxplore.com/news/2023-12-boosting-faith-authenticity-source-software.html
Trick prompts ChatGPT to leak private data

While OpenAI's first words on its company website refer to a "safe and beneficial AI," it turns out your personal data is not as safe as you believed. Google researchers announced this week that ...
https://techxplore.com/news/2023-12-prompts-chatgpt-leak-private.html
Defending your voice against deepfakes
Recent advances in generative artificial intelligence have spurred developments in realistic speech synthesis. While this technology has the potential to improve lives through personalized voice ...
https://techxplore.com/news/2023-11-defending-voice-deepfakes.html
Are your Cyber Monday purchases legit? There's (going to be) an app for that
Receiving a bogus designer handbag or imitation Wagyu beef might infuriate a Cyber Monday consumer, but a knock-off respirator or a fake pacemaker could imperil them.
https://techxplore.com/news/2023-11-cyber-monday-legit-app.html
Researchers break Apple's new MacBook pro weeks after release

A Georgia Tech researcher has successfully evaded security measures on Apple's latest MacBook Pro with the M3 processor chip to capture his fictional target's Facebook password and second-factor ...
https://techxplore.com/news/2023-11-apple-macbook-pro-weeks.html
Cloud data storage security approach taps quantum physics

Distributed cloud storage is a hot topic for security researchers around the globe pursuing secure data storage, and a team in China is now merging quantum physics with mature cryptography and st...
https://techxplore.com/news/2023-11-cloud-storage-approach-quantum-physics.html
Blockchain: A game changer for the insurance industry and people's well-being
Blockchain, a disruptive technology of our time, holds the potential to change our lives for the better. The insurance sector is a prime illustration.
https://techxplore.com/news/2023-11-blockchain-game-changer-industry-people.html
